
Thodoris Kouleris
Software Engineer

How SSH (Secure Shell) Works
Why SSH (Secure Shell) Exists
The most well-known application for remote management of a computer since the 1960's was Telnet. In fact, its popularity was such that even in the early 2000, there were network devices using Telnet for remote management.
The problem, however, was that Telnet had no encryption, meaning that anyone with a packet sniffer could intercept passwords or any information exchanged between two points.
SSH solved this exact problem. Tatu Ylonen, another Finnish figure in computer history, gave us the first version in 1995. He chose port 22 because it was between port 23 for Telnet and port 21 for FTP. SSH was using cryptography to secure the data transmission.
How SSH Works
The communication begins with the typical SYN, SYN/ACK, ACK handshake. Then they exchange the version that are going to use and the cryptographic algorithm. Immediately after, the public keys are generated and exchanged, since SSH uses asymmetric encryption. The pair of public-private keys that are going to use are ephemeral. Once both sides agree, the first packet is sent.
This usually happens over TCP, though it is not necessarily limited to TCP. To achieve this, the data being sent needs to be broken into smaller packets. Each of these packets contains the information the other end of the communication needs to reassemble the original data.
Each packet, therefore, has a header with the packet's size. Then, a section is dedicated to indicating the size of the packet’s padding. After that, the payload is included, which is the data the computer needs to receive. Finally, there’s the padding, whose size is revealed in the second section of the packet, along with some bytes for authentication.
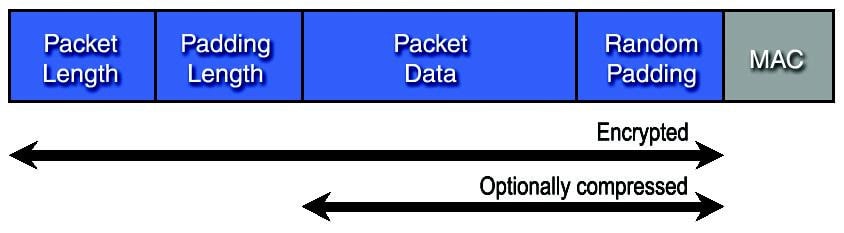
The encryption takes place in 4 of these sections of each packet: the header, the section revealing the padding size, the payload, and the padding itself.
Each packet is sent from one side of the connection to the other using one or more channels. When the other side receives the packets, it decrypts them and combines the payloads of each packet to obtain the final data.
In SSH, there can be more than one channel. Each channel serves a different purpose, for example, one for the session, another for authentication, etc.
How Asymmetric Encryption Works
In asymmetric encryption, we have two keys: the public key and the private key. The private key is the one we never share with anyone. The public key is the one we give to anyone who wants to communicate with us.
In this way, asymmetric encryption ensures that someone can send us any message, and only we can read it.
Conclusion
SSH was truly a revolution in the way we remotely manage computers. Unlike Telnet, which had serious security issues, SSH offers a secure communication method, protecting data from any kind of interception. With the use of encryption and asymmetric encryption, it became the standard for secure connections and network communications. Today, in addition to system management, it is used to ensure data protection in many other services, making it an essential tool for securing modern networks.